Corsair Flash Padlock 2 USB Flash Drive Vulnerability
Corsair has issued a press release announcing the discovery of a security issue that exposes data on their Flash Padlock 2 USB Flash Drive. The drive uses a keypad to allow users to enter a PIN in order to unlock data on the drive. The announced vulnerability allows anyone to access the data on the drive without knowing or entering the correct PIN. In the press release Corsair included a 10-step process that must be undertaken by the end user in order for the drive to “meet its security specification”, which presumably means to keep the data secure from those without knowledge of the PIN.
Interestingly enough, this second version of the keypad-protected device is also the second version released by Corsair that suffers from a critical security failure. As The H reported in 2008, the original Padlock from Corsair could be breached by simply opening up the device, attaching an external power source, and reading the data – which was unencrypted – from the memory stick.
This should serve as yet another reminder that external authentication factors – including biometric identification, PINs entered via external keypads, or voice recognition – are no substitute for a solid security architecture.
As always, stay safe and avoid a false sense of security.
Kingston Acknowledges Security Vulnerability in Hardware, SanDisk to Follow?
Back in December I wrote about Kingston acknowledging that a number of Kingston’s secure USB flash drives had been hacked. Yesterday, Kingston issued a press release announcing they would “replace affected secure USB flash drives with upgraded security architecture, new drives”. For a company that operates on lean margins this has got to be a huge expense, one that would only be incurred if there was no other choice. In issuing this press release, Kingston has effectively acknowledged that the security vulnerability plaguing its devices is the result of a fatal design flaw, not a software issue that could be resolved with a downloadable patch.
In terms of their replacements, Bob has learned that the new devices will be available around the end of January and will be much slower than the units they are replacing, with data transfer rates of about 5MB/sec. They will be based on entirely new hardware with an entirely new design architecture. Given the speed with which these devices are becoming available it is reasonable to assume that these were to be the next phase of secure USB flash drives to be sold by Kingston, though the transfer rates bring into question whether they have been fully optimized.
The fact that Kingston has issued a total recall of their affected secure usb flash drives brings up another interesting issue. As reported before, SanDisk secure USB flash drives have been hacked, as well as similar devices made by Verbatim. All three companies’ devices share a similar vulnerability, revealed around the same time, and yet SanDisk and Verbatim maintain that a software update is sufficient to render their devices once again secure. Either the differences in implementation between these devices are significant enough that SanDisk and Verbatim have dodged a bullet, or they are avoiding making the tough decision to issue a full recall.
These companies bear watching to see if they will come to the same, painful conclusion that Kingston has reached, or if they will be able to resolve their problems in a less costly manner.
As always, stay safe and avoid a false sense of security.
SanDisk Cruzer Enterprise Secure USB Flash Drive Hacked
Less than 24 hours after reporting that Kingston’s secure USB flash drives have been hacked, it appears that SanDisk’s secure USB flash drives have been hacked as well. According to SanDisk, they have “recently identified a potential vulnerability in the access control mechanism” for their Cruzer Enterprise series of flash drives. Given that access control is literally the key to any secure environment, it seems safe to interpret this as the “corporately correct” way of saying that SanDisk Cruzer Enterprise devices have a security hole.
This calls to mind a previously detailed SanDisk Cruzer Enterprise secure USB flash drive vulnerability.
Here is the relevant text from SanDisk’s website that covers this newly reported vulnerability:
***
Security Bulletin December 2009
Overview
The Cruzer® Enterprise series of USB flash drives are equipped with a hardware-based encryption module and an access control mechanism to protect company data. SanDisk has recently identified a potential vulnerability in the access control mechanism and has provided a product update to address the issue.
Important Note: This issue is only applicable to the application running on the host and does not apply to the device hardware or firmware.
As a result, all Cruzer Enterprise USB flash drives being shipped to customers as of today contain the product update. SanDisk has also taken measures to inform customers and channel partners about the issue and has provided a software product update online to secure existing Cruzer Enterprise USB flash drive devices.
Devices to which this change applies
- Cruzer® Enterprise USB flash drive, CZ22 – 1GB, 2GB, 4GB, 8GB
- Cruzer® Enterprise FIPS Edition USB flash drive, CZ32 – 1GB, 2GB, 4GB, 8GB
- Cruzer® Enterprise with McAfee USB flash drive, CZ38 – 1GB, 2GB, 4GB, 8GB
- Cruzer® Enterprise FIPS Edition with McAfee USB flash drive, CZ46 – 1GB, 2GB, 4GB, 8GB
***
It should be noted that, as with the Kingston secure USB flash drive hack, this vulnerability impacts FIPS validated flash drives, which are marketed to U.S. and Canadian government agencies and thus should be considered the most secure of the devices offered by these companies.
As a little background, the FIPS 140-2 certification is divided into four possible security levels, the highest of which is Security Level 4. Currently, the highest level of FIPS 140-2 validation available for flash drives is Security Level 3, offered by only a few vendors. Security Level 3 is the first level that includes tests for physical security and/or tamper detection-response circuitry, designed to “zeroize” all plaintext critical security parameters (CSPs). However, both of the compromised series of devices offered by Kingston and SanDisk had FIPS products that had only been validated to Security Level 2, which does not include this critical requirement.
In resolving this issue SanDisk claims to have taken measures to inform customers and channel partners, and has provided a software product update online that purportedly fixes the problem.
As always, stay safe and avoid a false sense of security.
Kingston Secure USB Flash Drive Hacked
It appears that Kingston’s secure flash drives have been hacked. In case the page changes, what follows is the information that Kingston is currently posting about the vulnerability of their DataTraveler series of secure flash drives.
***
Kingston’s Secure USB Drive Information Page
It has recently been brought to our attention that a skilled person with the proper tools and physical access to the drives may be able to gain unauthorized access to data contained on the following Kingston Secure USB drives:
- DataTraveler BlackBox (DTBB)
- DataTraveler Secure – Privacy Edition (DTSP)
- DataTraveler Elite – Privacy Edition (DTEP)
***
Looking through this list it will be interesting to see if DataTraveler BlackBox will maintain its FIPS 140-2 Level 2 certification, an important qualifier for government purchasers in the United States and Canada.
If you own a Kingston it appears the only way to correct this flaw is to send your flash drive back to Kingston for a factory update, during which all data will be erased. While Kingston has acknowledged the flaw in their secure products, they do not appear to have taken the step of issuing a general recall of all compromised devices. As of yet there is also no indication as to whether large-volume or other registered customers will be notified of the vulnerability.
As always, stay safe and avoid a false sense of security.
Lexar JumpDrive Secure Vulnerability
Cruising through the archives I came across this report on a major Lexar JumpDrive Secure vulnerability. The password to the device is “encrypted” by xoring it and storing it in the nand flash. It’s trivially decipherable.
It’s an older example, but shows how a product called “Lexar JumpDrive Secure” simply isn’t secure, and professional cryptographers were clearly not involved in the design and implementation of the product.
As always, stay safe and avoid a false sense of security.
Another Biometric Flash Drive Vulnerability
Here’s a link to an article about a number of easy to crack biometric flash drives brought to light by the folks at Heise Online. This vulnerability in two of the controllers from Afa Technology, a.k.a. Afatech, effects flash drives from the following vendors:
- 9Pay
- A-Data
- Transcend
Given that flash drive vendors often use controller chips manufactured by third parties, it is likely that additional biometric flash drive vendors harbor this same vulnerability. Afatech recently merged with another Taiwan-based IC company, ITE Tech, and press releases indicate their controller design team will be integrated into a similar R&D team at ITE Tech. Therefore, any purchases of biometric flash drives from vendors that use controllers from Afatech or ITE Tech should be scrupulously reviewed.
As always, stay safe and avoid a false sense of security.
Fake Kingston Flash Drives
Here’s a link to an interesting post on fake Kingston flash drives being sold on eBay. This is a good reminder to always buy flash drives (or any portable media) that are labeled with individual serial numbers, preferably directly on the drive itself. A call to the vendor is also a good idea, especially when purchasing in bulk.
This security professional is going to make some calls right now….
As always, stay safe and avoid a false sense of security.
Vulnerability Analysis of Secure USB Flash Drives
Here is a link to a cool vulnerability analysis of secure USB flash drives that unveils no less than four vulnerabilities in various products. It also offers solutions that all six manufacturers could have applied to prevent these vulnerabilities.
Here is a list of the vendors and their products containing the vulnerabilities mentioned:
ATP Electronics – ToughDrive
Samsung Electronics – SUM-2GTB
Samsung Pleomax – SPUB S50
LG Electronics – Mini Slide
Imation – iFLASHSLIM
SanDisk – Cruzer Micro
As always, stay safe and avoid a false sense of security.
Raidon Staray-S Series Cracked
Here’s a link to a recent and well-documented cracking session by Christiane Rütten at The H Security. In it the Staray S325, put out by Raidon, is found to have multiple vulnerabilities and is thoroughly cracked. The moral of the story: even hardware encryption is of no benefit if implemented on budget drives with poor encryption.
http://www.h-online.com/security/Cracking-budget-encryption–/features/112548
As always, stay safe and avoid a false sense of security.
MXI Attempts To Block Malware But Doesn’t Get It Quite Right
Perhaps in a response to Bob’s analysis of the MXI Stealth MXP device, the manufacturer has responded with a technology that purports to prevent malicious code from being written to the “read only” partition of their Stealth MXP secure hardware encrypted flash drive.
In a very strangely worded press release on February 17, 2009, the company announced “MXI Security Expands Lockdown Delivery Service to Help Enterprise Customers Fight Malicious Software”. This allows enterprise customers to use their ACCESS Enterprise software to set a “unique management code” that guarantees that the software on devices cannot be modified by anyone except the end customer.
We tested this functionality on a Stealth MXP device. Basically a user or administrator can set a code or password which must be entered correctly when performing a software update to the “read only” partition. We set this access code, and then tried to update the software on the “read only” partition. As advertised, the software update was not successful without first entering the access code.
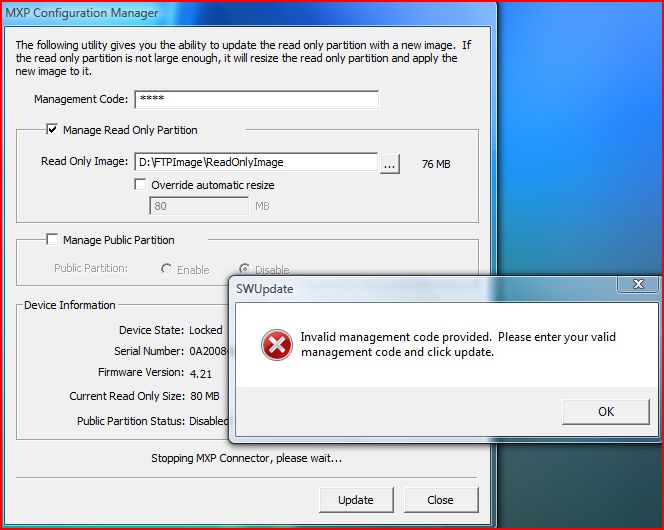
However, we also determined that this access code is not protected against brute force password guessing! Unlike the device password, it seems that you can try an infinite number of access codes. We tried an incorrect code 100 times, and then we entered the correct code, and the device again allowed us to load malicious software onto the “read only” partition.

It’s strange that a security company would miss out on such an obvious vulnerability. Any attacker wishing to infect a user’s device with malware could do a brute force attack on the access code of the device in order to overwrite the “read only” partition.
Even if the devices correctly prevented a brute-force password guessing attack on the access code, this still would not prevent a malicious attacker from infecting their own new device, and leaving it in the company parking lot where an employee might pick it up and plug it in to an internal company computer.
I agree with Bob’s initial comment that secure devices should actually require a valid digital signature on the software before allowing an update to happen.
As always, stay safe and avoid a false sense of security.